Gain unprecedented visibility into malicious cyber threats and activities threatening your business with timely information.
A modular, enterprise-grade platform that provides the most comprehensive set of cyber threat intelligence solutions and advanced security controls, allowing for tailored protection and scalability for the most demanding environments.
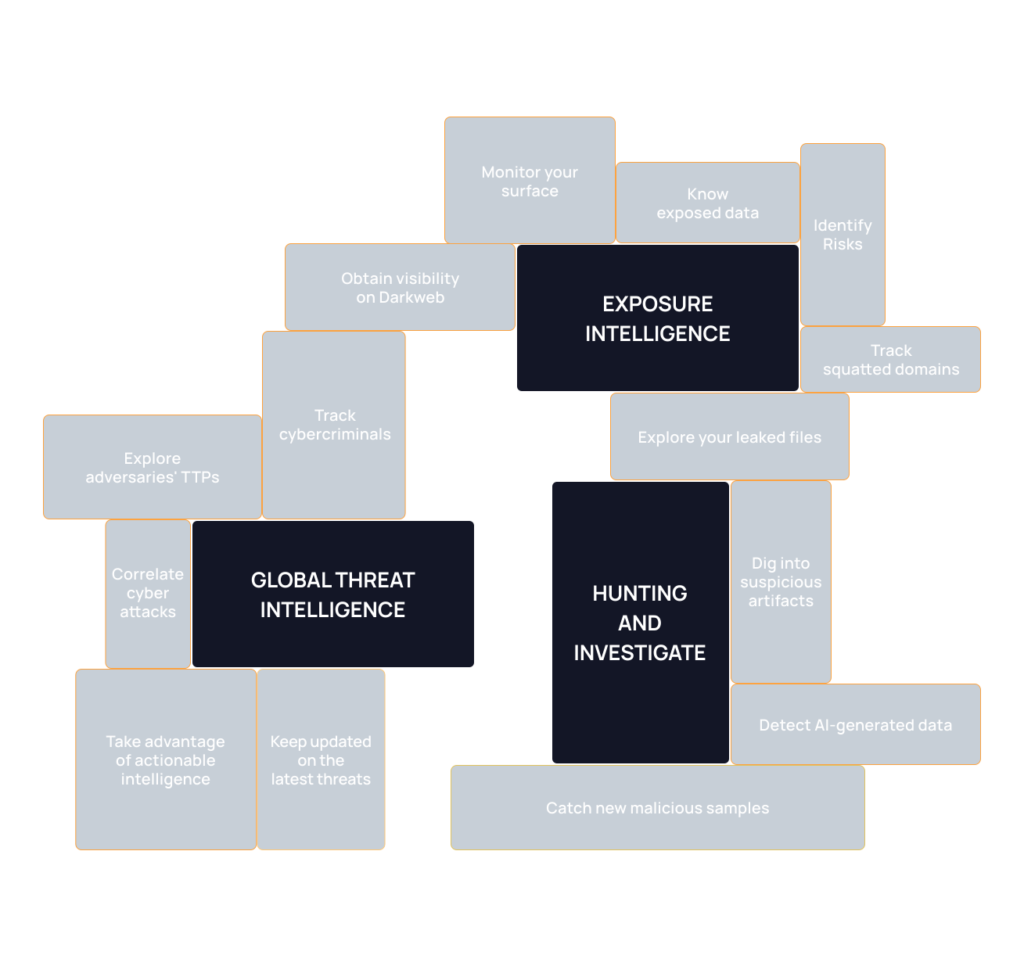
Take advantage of the accurate information generated by the team to expedite your incident prevention and response activities.
Make informed and fast decisions to secure your assets and stakeholders.
Leverage the flow of threat data to enhance the accuracy and timeliness of your threat detection.
REPLICATE OFFICE CYBERSECURITY CONTROLS IN ALL REMOTE LOCATIONS WITH NETWORK EDGE SECURITY

Secure IoT router easily connected to employees' Wi-Fi

App for an ultra fast set up process and cybersecurity insights

Sleek web-tool for policy implementation and monitoring

Secure AI solution powered by Cluster25 threat intelligence

DuskRise has partnered with Google Cloud’s Work Safer program, to provide businesses with everything necessary to enable secure collaboration. Google launched Work Safer to keep organizations of every size secure with a cloud-first, zero trust model. Learn more