RuRAT used in spear-phishing attacks against media organisations in United States
By Cluster25 Threat Intel Team
March 3, 2022

INTRODUCTION
On 23.02.2022 one of our partners received a very specific targeted spear-phishing email message which leads into luring the victim to download fake video chat application. The infection chain appears to be composed of 2 (two) stages: a first one in which the victim receives an email containing a URL that leads to the download of a malicious MSI installation package. A second one in which the MSI installation package goes download a copy of the RuRAT malware along with the legitimate Trillian application.
INSIGHTS
The email message was well crafted into tricking the victim towards clicking the link attached to the body of the message. The full body text of the message is shown below
“Hello, we are a group of venture capitalists investing in promising projects. We saw your website and were astounded by your product. We want to discuss the opportunity to invest or buy a part of the share in your project. Please get in touch with us by phone or in Vuxner chat. Your agent is Philip Bennett. His username in Vuxner is philipbennett Make sure you contact us ASAP because we are not usually so generous with our offers. Thank you in advance!“
Once the victim clicks the link attached to the email it will be redirect him into the following landing page controlled by threat actor. Following we report a screenshot about how the malicious page appears to the user:
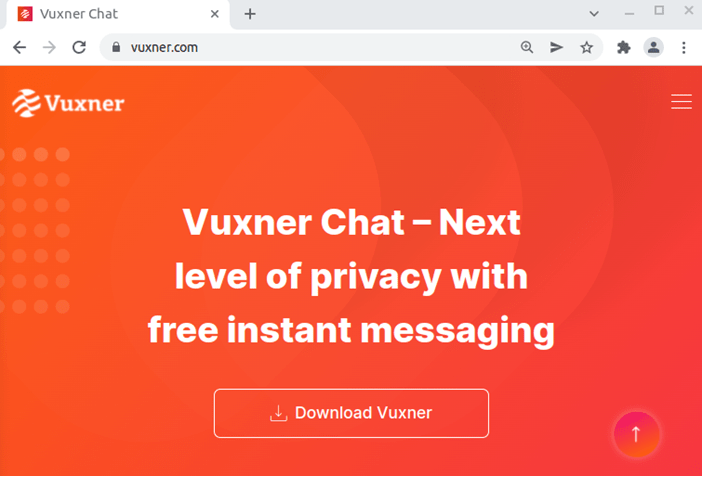
According to the historical data the domain www[.]vuxner[.]com was registered during the year of 2021 around July through NameCheap.

According to an analysis performed through the investigation module of our analysis platform, it is possible to observe that on 21.07.2021 a first A record was assigned to this domain. On 27.10.2021 the domain name was subsequently updated and protected through the Cloudflare service. However we manged to find the real IP address hidden behind the Cloudflare proxy and found evidences that suggest the 86.104.15[.]123 as the real malicious one used in this campaign. This IP address appears to belong to the provider Fast Serv Inc. d.b.a. QHoster.com according to the following details:

INFECTION CHAIN
Infection chain for this campaign can be divide in a fist stage phase, where the decoy URL drops and installs a Software called “Trillian” and the second one where the installer drops a legitimate Remote Desktop Software known as RuRAT used for malicious purposes. Once the victim clicks on “Download Vuxner” on the decoy website, the webiste is designed to serve a very large file (55MB in size) named “VuxnerChat.exe”. According to extracted evidences application was created with Setup Factory 9.0.
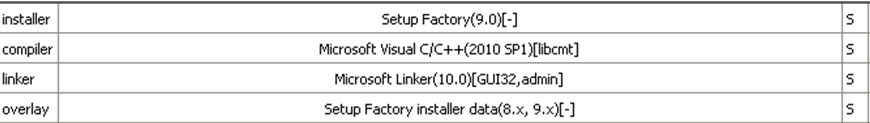
When the victims executes VuxnerChat.exe the process begins by installing a legit software “Trillian” which the threat actors have tampered with .MSI package and changed the name to “Vuxner Trillian Setup”.

During the process of installation it creates a new folder “C:Program Files (x86)Vuxner LtdVuxner Trillian” where it drops 2 files 1.bat and trillian.msi
Code snippet for 1.bat:
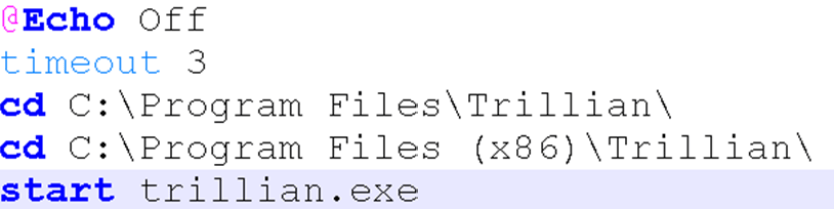
After clicking “Finish” in the Wizard installation the infection will move into downloading the second stage dropper called “setup.exe” from the link https://www.vuxner[.]com/setup.exe, where it drops into %temp% and starts extracting all belonging files under the path “C:swrbldin”.
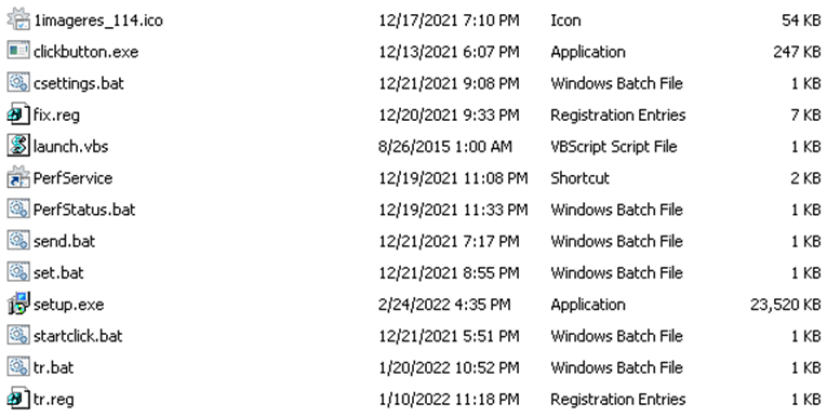
It changes the attributes of the the folder into “hidden“. Each dropped file have a set of commands to follow, reported below:
- fix.reg : contains the XML-configuration of the RuRAT specifying to import that configuration in HKEY_LOCAL_MACHINESOFTWAREUsorisRemote Utilities HostHostParameters
- tr.reg: contains the link to the Trillian installer specifying to import that configuration in HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerStartupApprovedStartupFolder
- set.bat: reg import fix.reg (XML-configuration) into the registry and delete C:Program Files (x86)Remote Utilities – HostLogs
- tr.bat: import tr.reg (link to the Trillian installer) into the registry. Delete C:Program FilesRemote Utilities – HostLogs and the uninstaller key HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionUninstall{9521E224-E4AA-4DA5-92A4-5AA6DFF2CEF1
- launch.vbs: Used to run an executable from arguments using Wscript.Shell object
- PerfStatus.bat: ensure that rfusclient.exe have only one instance of execution (if procnum > 1, taskkill the other instance)
- send.bat: check if sanisinst.exe generates error, in case of errors exit
- startclick.bat: used to run the clickbutton.exe (loader of a PE executable) to run the sanisinst.exe (passed as parameter)
After all files are dropped and executed it will popup to the user where it asks for permission to install Remote Access Software RuRAT. Taking look at tr.bat we found this specific GUID “9521E224-E4AA-4DA5-92A4-5AA6DFF2CEF1” by checking MSIGUID at Remote Utilities Host official site and we found the exact version which is being dropped into infected device.

After full infection is completed it will connect to Command and Control at IP: 192.119.14[.]178 on TCP port 5655.
INDICATORS OF COMPROMISE
Files:
| MD5 | Filename |
| 584b3ed25c9a93a5582567357d513b8c | VuxnerChat.exe |
| cf4d5c9e572a137799da6d1eced03a6a | 1.bat |
| e415a80c4cc3cfb9a0ef61a7590e112d | trillian.msi |
| b1d096094b5a54aac6249455c657b9ec | 1imageres_114.ico |
| 68dfcd6c336f7a20a8060b19fba07178 | PerfService.lnk |
| 81e2830297b250268d3e9aeeda36570d | PerfStatus.bat |
| 5c1f7feae3e1d5143cf84e5cde9e9ee5 | clickbutton.exe |
| 481c49351cfec4d0b70f28365b3cb2ad | csettings.bat |
| af208f2b676077b2a3f1c2927db4c74c | fix.reg |
| c578d9653b22800c3eb6b6a51219bbb8 | launch.vbs |
| 302539ac546a2b92f284012f8e00c2f4 | sanisinst.exe |
| 25fc468f5ecb6f9d70bffd0e8e4fc6da | send.bat |
| f580dd7d29c0c4902bb81a7b4911e06e | set.bat |
| ec64d3d5d430772405071c3b6404b881 | setup.exe |
| 0658feb206ac164b59123a2cbcc7ad47 | startclick.bat |
| 8b1df5a245d627960ea4a745dfc71a32 | tr.bat |
| 88b355a0b4af7338733739747c3d4c9e | tr.reg |
Network:
| TYPE | VALUE |
| IPV4 | 192.119.14[.]178 |
| IPV4 | 86.104.15[.]123 |
| DOMAIN | vuxner[.]com |
| HOSTNAME | www.vuxner[.]com |