

Cybersecurity is a critical concept to take into consideration in the chemical sector given the potential consequences a successful cyber attack would create. This is a sector that has its main core in the production of chemicals then used in a wide range of industries, from healthcare to transportation, to agriculture and other sectors. An attack against any company working in this sector, with the production of these chemical products could have as a consequence the release of hazardous material in the environment, representing also a risk to people and animals. Another consequence of a cyberattack against this sector could also disrupt strategic critical infrastructure and cause economic damage to a wide range of interconnected companies in a certain country.
In fact, the chemical sector is definitely considered a critical infrastructure with strategic goals, making it an attractive target for any malicious actor. This is a sector often interconnected with other pivotal sectors, such as energy production and water lines, and it is a critical part of the industry also because it deals with sensitive information linked to the research and development of chemical formulas, the creation of new production processes, and also customer data, making it a perfect target for industrial cyber espionage and intellectual property theft from other countries.
In the EU, the chemical sector is regulated by different laws more or less related to cybersecurity. The main framework where any company has to abide by is the General Data Protection Regulation (GDPR), that even if primarily deals with data protection and privacy, it also includes different provisions related to cybersecurity, requiring companies to take measures to ensure the security of personal data, and how it should be stored and processed within their cyber perimeter.
There are also other laws that are regulating the European chemical sector.
The NIS2 Directive, a EU-wide policy on cybersecurity that came into force in 2023, provides legal measures to boost the overall level of cybersecurity in the European Union, establishing a framework for the management of the eventual cybersecurity risks and incidents, creating requirements for EU member states and digital service providers working in the European territory of EU. The directive also creates a cooperation network among member states and establishes a single point of contact for reporting and sharing information on cybersecurity incidents.
Another law affecting the chemical sector is the EU Cybersecurity Act, that came into force on June 27, 2019, introducing a EU-wide cybersecurity certification framework, it created the European Cybersecurity Research and Competence Centre, and the European Cybersecurity Certification Group. The act also enhances the role of the EU Agency for Cybersecurity (ENISA). This regulates the chemical sector because it affects ICT products, services and processes.
There’s also another legislation that even if it is not directed to cybersecurity, the Chemicals Regulation (REACH), this governs the registration, evaluation, authorization, and restriction of chemicals in the European Union, and even if it does not specifically address cybersecurity, it does require companies to provide and store information on the hazards and risks associated with the chemicals they produce or use, which may lead to a data leak if the logistics of the data storage or transfer are badly handled.
We take some case studies to provide specific examples of attacks against the sector scope of this brief.
In 2014, DuPont, an American multinational chemical company, disclosed a data leak scandal of sensitive and private company data, including trade secrets related to the production of titanium dioxide, used to make the pigment for the colour white, that happened within the company. This case was an example of insider threat, in fact as documents and testimony in a 2014 federal trial in San Francisco reveal, a naturalised American citizen stole DuPont’s protocols for producing its superior titanium white from 1997 through 2011, thus being responsible for selling classified documents to companies controlled by the government of the People’s Republic of China (PRC).
In 2019, Norsk Hydro, a Norwegian aluminium company, was attacked by ransomware, LockerGoga, forcing them to shut down some of its production facilities. The attack is believed to have originated in Russia, affecting all 35,000 Norsk Hydro employees across 40 countries, locking the files on thousands of servers and PCs. The financial impact would eventually approach $71 million. All of that damage had been set in motion three months earlier when one employee unknowingly opened an infected email from a trusted customer.
Another interesting case is the ransomware attack that targeted the German chemical distributor Brenntag, in May 2020, carried on by the hacking group called DarkSide. The company’s IT systems had to be shut down in order to contain the attack, and this affected the company’s operations in several EU regions. To restore its systems, the company had to pay 4.4 million dollars to the criminal group. Regarding the intrusion vector, one of DarkSide’s members claimed to have managed to get access to the network after purchasing stolen credentials.
Private data leak page sent to Brenntag after 2020 ransomware attack
Again in 2020, the German chemical company Lanxess was targeted by a cyberattack that disrupted its IT systems and caused production delays. The attack is believed to have been carried out by a Chinese hacking group called WinNTI, an Advanced Persistent Threat (APT) likely affiliated to the Chinese Government, and is thought to be part of a larger espionage campaign targeting the chemical industry.
In May 2021, Italian chemical company Radici Group was hit by a ransomware attack that disrupted its operations. The attackers, the Russian speaking group BlackBasta, demanded a ransom payment in Bitcoin to restore the company’s systems. According to the Tactics, Techniques and Procedures (TTPs) used by BlackBasta, as per Norsk Hydro incident, also in this case the initial vector was a spear phishing email opened by an employee, containing the entrypoint of the infection chain.
BlackBasta infection chain [source: Kroll.com]
In August 2021, the Oil and Gas company Shell disclosed that it had suffered a cyberattack that impacted some of the company’s operations in the Netherlands. The hackers managed to target a specific piece of hardware with previously-unreported vulnerabilities. Once they breached the vulnerable servers the hackers began exfiltrating data.The company stated that it had isolated the affected systems and launched an investigation into the incident.
Finally, in the late 2022, different companies in the chemical industry based in Europe, Asia, Middle East and South America are targeted by hacking attempts from different malicious actors, including Advanced Persistent Threats (APTs), that are oftenly state-sponsored groups. An espionage campaign led by one APT, the North Korean state-sponsored hacking group, Lazarus, was discovered in November 2022 a campaign targeting the networks of a number of organisations operating in different sectors, including the chemical one. The group was using many attack vectors, from spear phishing mails to vulnerability exploitation in order to install the popular DTrack malware and steal logins, credentials and intellectual property.
Timeline of the mentioned attacks
During the analysis we conducted a quick research about the possible risks of some of the major European companies operating in the chemical sector, in terms of exposed credentials and vulnerabilities. For the research we chose a sample of 25 players operating in the analysed sector.
Regarding the exposed credentials, 79% of the analysed companies have at least one credential belonging to their employees publicly exposed. As known, most of these credentials are stolen from data breaches occurred on third party sites, so it is possible that almost all of them are useless for obtaining an access on a company’s asset. This could be due to the fact that, hopefully, the password used on an internal asset is different from the one used on a third party site.
Beyond the direct access to the company’s assets, don’t forget that publicly exposing employees’ emails could represent a risk due to the fact that a malicious threat actor could easily retrieve from the data breach a list of email addresses used as targets for an initial attack against the company.
In other cases, the data from the breaches is publicly released after a long period of time and a company could have a password policy which imposes the password to be changed after a certain amount of days, making the exfiltrated credentials useless even if the exfiltrated password was the same of the one used for the company’s assets.
However, according to our results, 68% of studied companies have at least one credential coming from data breaches published in 2023, so in the last 3 months. This could increase a bit the possibility of having the same password for internal and external portals, since the password policy usually expects the change to be made every 90 or 180 days.
Regarding the external perimeter of the studied companies, the data is encouraging. Just 16% of the sample have at least an exposed vulnerability. The oldest vulnerability found is CVE-2006-20001 affecting Apache server, having a base score of 7.5. The most frequent vulnerability seems to be 2022-31629 affecting the PHP software and having a base score of 6.5. Finally, the most dangerous vulnerabilities found are CVE-2022-31813 and CVE-2022-22720, both affecting the Apache server and having a critical base score (9.8).
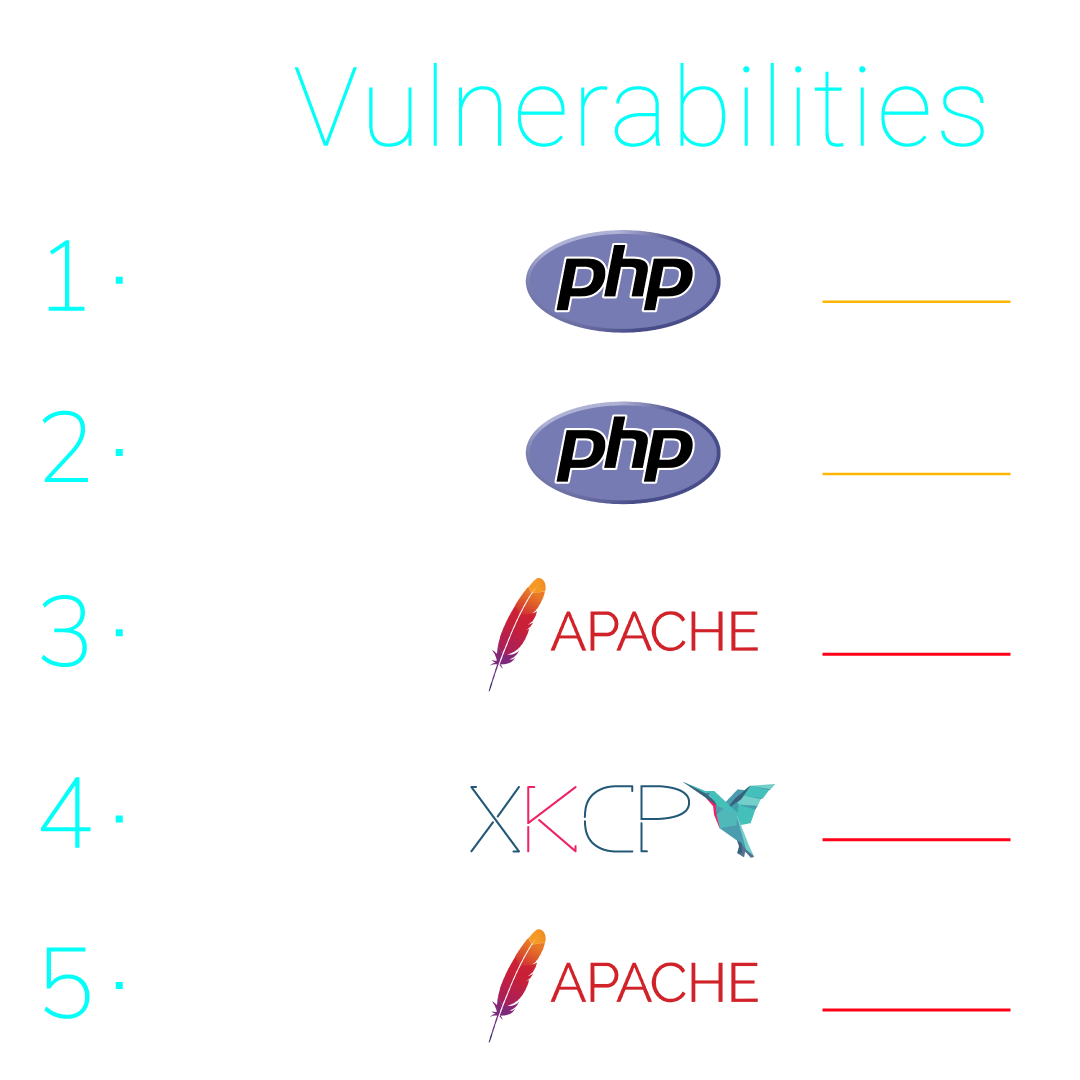
Most frequent vulnerabilities found during the study
From our study, fortunately, we didn’t find any open RDP (3389) port on the analysed companies sample. Exposed RDP server are one of the most exploited way by ransomware groups that, in combination with stolen credentials of a targeted company, can find an easy access to the internal network.
These attacks are just significant examples of cyber-attacks on critical infrastructure, highlighting the growing threat of cyber-attacks on critical infrastructure and the need for improved cybersecurity measures to prevent such attacks from occurring in the future.
Any company should take proactive measures in order to prevent cyberattacks and to have a robust cybersecurity strategy in place to protect their operations and sensitive information. To mitigate the cyber threats, and avoid replicating the above mentioned examples there are certain steps any company should take.
Before anything, for the company it is important to understand and identify all its assets, data and systems that are the most critical to the business and assess any risk that could happen to each one.
The company should also implement strong policies for regulating the access to its premises and to its data by employees and visitors. The data should be encrypted and there should also be data backup systems.
It is vital to conduct regular security training for all the employees, as it is important to do regular security audits and assessments to all the company resources. And as last resort, having an incident response plan, to limit the damages of a cyber accident of any sort.
Sources:
https://digital-strategy.ec.europa.eu/en/policies/nis2-directive
https://digital-strategy.ec.europa.eu/en/policies/cybersecurity-act
https://ec.europa.eu/environment/chemicals/reach/reach_en.htm
https://www.cnbc.com/2014/07/11/us-man-gets-15-years-for-china-linked-espionage.html
https://www.justice.gov/opa/pr/two-individuals-and-company-found-guilty-conspiracy-sell-trade-secrets-chinese-companies
https://news.microsoft.com/source/features/digital-transformation/hackers-hit-norsk-hydro-ransomware-company-responded-transparency/
https://www.bleepingcomputer.com/news/security/chemical-distributor-pays-44-million-to-darkside-ransomware/
https://www.pandasecurity.com/en/mediacenter/news/winnti-hacker-attack-dax-company/
https://sigmaawards.org/winnti-attacking-the-heart-of-the-german-industry-2/
https://hackerjournal.it/10149/radicigroup-colpito-da-attacco-ransomware-blackbasta/
https://kroll.com/en/insights/publications/cyber/black-basta-technical-analysis
https://www.forbes.com/sites/leemathews/2021/03/23/oil-giant-shell-victimized-in-december-2020-hack/
https://securelist.com/dtrack-targeting-europe-latin-america/107798/